If you’ve ever worked with API integrations, you’ve probably come across API keys. They’re a common way to identify and authorize access to services, but they’re often misunderstood or implemented insecurely. Understanding how they work is essential for any developer dealing with inter-system communication, as mismanagement of these keys can lead to data leaks or API misuse.
Before the emergence and popularization of API keys, several authentication and access control methods were used to protect APIs. Although some approaches were quite basic, they met the needs of the time, especially in less complex systems and less exposed to the internet. One of the most widely used methods was Basic Authentication where user credentials were sent in the HTTP header.
Authorization: Basic base64(username:password)In addition to exposing user credentials directly in requests made to the APIs, it was not possible to perform access control by consumer application. Therefore, the only way to remove access from a specific application was to revoke the user’s credentials, which was not a practical solution.
What are API keys?
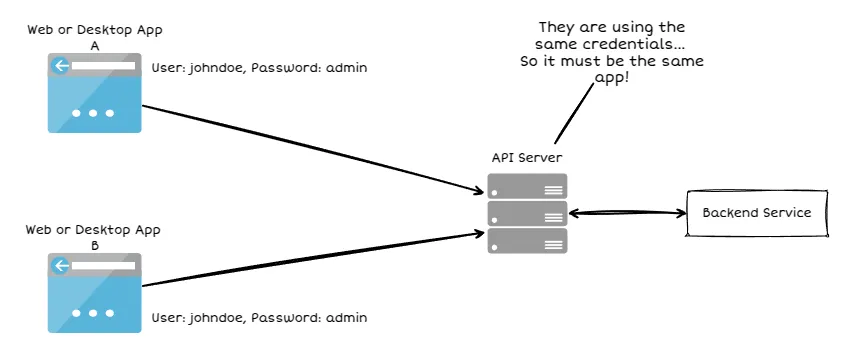
In order to reduce the exposure of user credentials and enable the identification of isolated applications. Instead of asking for credentials, API providers have started issuing unique identification codes for each client application.
These unique identifiers are what we call API keys. They allow the server to know who is making the request and whether that request is authorized.
Unlike more robust mechanisms like OAuth 2.0 and JWT, which offer user-based authentication and granular permissions, API Keys are simpler and faster to implement. However, precisely because of this simplicity, it is important to use them carefully to avoid security risks.
It should be noted that when using API keys we are dealing with identification and not authentication. This means that API keys only allow us to identify who is calling but do not guarantee that the calling program is who it says it is.
Well… after reading this, it may seem like API keys are not reliable tools to use… But you need to keep in mind that they are perfect tools if they are used to solve the problems they were designed for. Among them we can mention: application identification, rate limiting, access control and request monitoring/auditing.
Let’s examine each of these use cases.
Using API keys for access control
At their core, API keys serve as a gatekeeper, allowing or denying access to your API based on predefined rules. When a request comes in, the system checks the provided key and determines whether it’s valid. But beyond just a basic pass-or-fail check, API keys can be fine-tuned for different levels of access. You can assign different permissions based on the key—some might allow full read and write access, while others might be restricted to read-only operations. This is especially useful in multi-tenant environments, where different users or applications require different levels of access.
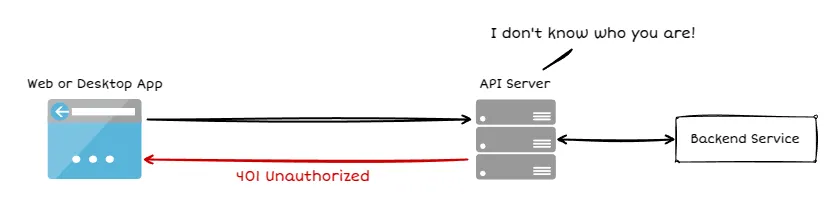
So while API keys are a great starting point for access control, they work best when used in combination with other security measures. They provide a lightweight way to manage API access but should be treated with care to avoid becoming a security liability.
Using API keys for rate limiting
One of the most common ways to implement rate limiting is by tying request quotas to API keys. When a request comes in, the system checks the key against a set limit—maybe 100 requests per minute for free-tier users and 10,000 per day for premium subscribers. If the key has exceeded its quota, the API returns a 429 Too Many Requests response, signaling the client to slow down. This prevents overuse and ensures fair access to resources.
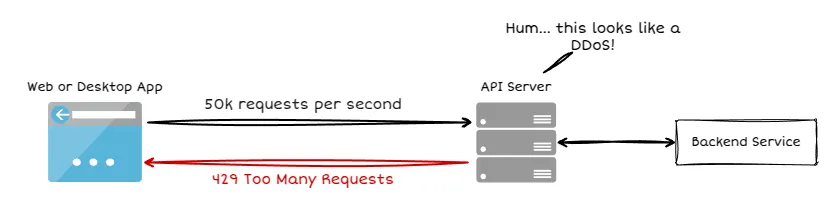
Rate limiting isn’t just about stopping abuse; it’s also about optimizing performance. Without limits, a poorly designed client or a malicious actor could flood your API with requests, causing downtime or degraded performance for legitimate users. By linking limits to API keys, you get precise control over how different users interact with your service. You can even implement dynamic rate limits, where an API key’s quota adjusts based on user behavior, subscription level, or real-time server load.
Using API keys to identify applications
Every time an app makes a request to your API, it sends its API key along with it. This allows your backend to instantly recognize which application is making the request, even if the user remains anonymous. This is useful in scenarios where multiple services, third-party integrations, or even internal applications are interacting with your API. By associating each app with a unique API key, you can track usage patterns, monitor behavior, and apply custom configurations on a per-application basis.
For example, let’s say you run an API that provides weather data. You might have different partners—one building a mobile app, another integrating with IoT devices, and a third using the data for analytics. By assigning each of them a unique API key, you can monitor which app is making the most requests, optimize performance for high-traffic clients, and even apply different rate limits or response formats based on the application type.
Using API keys to monitor requests
Since every request to your API includes an API key, you can log and track activity on a per-client basis. This means you’re not just collecting generic traffic data—you’re getting precise insights into how each individual user or application interacts with your API. This is incredibly useful for performance monitoring, debugging, and even security investigations.
For instance, let’s say you notice a spike in failed authentication requests. By checking your logs, you can see exactly which API key is responsible, helping you determine whether it’s a misconfigured client or a brute-force attack attempt. Similarly, if an API key is making an unusually high number of requests in a short period, that could indicate abuse, a coding error, or even a security breach.
Auditing goes beyond just monitoring—it’s about creating an accountability trail. When API keys are properly logged, you have a record of every request made, including who made it, when, and what endpoint they accessed. This is crucial for compliance with regulations like GDPR, LGPD or HIPAA, where tracking data access is a legal requirement. If a security incident happens, your logs can help reconstruct the event, pinpointing exactly what went wrong and how to prevent it in the future.
Beyond security, request monitoring with API keys also helps with usage analytics and optimization. You can analyze API traffic to identify the most popular endpoints, track latency issues, or even adjust pricing models based on actual usage patterns.
API key types
API keys can be grouped into two main types depending on how they’re used. First, there’s the environment-based category, where keys are either public (used in client-side apps) or private (kept secret on the backend). Then, there’s the functionality-based category, which includes static, expiring, scoped, signed, and ephemeral keys—each designed for different levels of security and control.
Let’s briefly explore each of these types.
Private API keys
Private API keys, on the other hand, should never be exposed. They’re used in secure environments, like backend servers, where they can be kept secret. These keys often have full access to the API, allowing actions like modifying databases, handling user authentication, or processing sensitive transactions.
Because of their power, private API keys should always be stored securely (e.g., in environment variables, secret management tools, or vaults) and never hardcoded into source code. If a private key gets leaked, an attacker could gain full control over the API, so regular rotation and access restrictions are key.
📌 Example Use Case:
A payment processing API where the private key is used to charge customers.
Pros: Full access and control over the API.
Cons: If leaked, it can be a major security risk.
Public API keys
Public API keys are meant to be exposed—they’re used in environments where hiding them is either impossible or impractical, like in frontend applications (web browsers, mobile apps, or client-side JavaScript). Since they’re visible to anyone inspecting the code, public API keys usually come with strict limitations to reduce security risks.
📌 Example Use Case:
For example, they might only allow access to non-sensitive data or be restricted to certain domains or IP addresses.
Let’s say you have a weather app that fetches forecasts from an API. The API key is included in the frontend code,
but it’s limited to read-only access and can only be used from your website.
Pros: Easy to use in client-side apps.
Cons: Can be exposed and misused if not properly restricted.
Static API keys (Long-Lived key)
Static API keys don’t expire unless manually revoked or rotated. These are commonly used for internal services or simple integrations.
📌 Example Use Case:
A weather API issues a static key to an application that fetches daily forecasts.
Pros: Easy to use, persistent.
Cons: Risky if exposed; needs manual rotation.
Expiring API keys (Time-Limited Key)
These API keys expire after a set period, making them ideal for temporary access.
📌 Example Use Case:
An e-commerce API provides a 24-hour API key for a partner company to sync its inventory.
Pros: Limited lifetime reduces security risks.
Cons: Clients need to request a new key periodically.
Scoped API keys (Permission-Based Key)
Scoped API keys have limited access, allowing for fine-grained permissions.
📌 Example Use Case:
A banking API issues an API key that allows reading transactions but not making payments.
Pros: More security, least privilege access.
Cons: Requires managing scope configurations.
Signed API keys (Cryptographically Secure Key)
Signed API keys include a cryptographic signature to ensure authenticity.
📌 Example Use Case:
A video streaming API requires requests to be signed using a private key before accessing premium content.
Pros: Prevents tampering; adds an extra security layer.
Cons: Requires more processing power.
Ephemeral API Key (Short-Lived Key for Each Session)
Ephemeral API keys are dynamically generated for each session and expire quickly.
📌 Example Use Case:
A gaming API generates a new key for each player session, expiring after logout.
Pros: Reduces risk of stolen keys being used long-term.
Cons: Clients need to request new keys frequently.
How to define an API key?
When providing an API, it’s our job to ensure that access to our services is both secure and easy to manage. To help with this, API keys can come in a variety of formats, depending on the level of security and compatibility required by the API provider. Some are simple and easy to use, while others incorporate encryption and signing mechanisms for extra security. Here’s a breakdown of the most common API key formats and where they’re typically used.
The different API Key formats
Not all API keys look the same. Depending on the level of security required, we generate keys in different formats:
Simple Alphanumeric Strings
This is the most basic type of API key—just a randomly generated string of letters and numbers. It’s easy to generate and implement but doesn’t offer any built-in security beyond being a unique identifier. These keys should always be used with access restrictions (like domain or IP whitelisting) to reduce the risk of unauthorized use.
abc123XYZ789UUID-Based Keys
Some API providers use UUIDs (Universally Unique Identifiers) as API keys because they are guaranteed to be unique across different systems. This format is useful for tracking API keys efficiently, as UUIDs are structured and standardized.
550e8400-e29b-41d4-a716-446655440000Base64 Encoded Keys
Base64 encoding is sometimes used to format API keys so they are easier to pass in URLs or headers without special characters causing issues. However, Base64 does not add security—it’s just encoding, not encryption.
YXBpX2tleV9zYW1wbGVfMTIzNDU=Hashed or Signed Keys
For added security, API keys can be hashed (using SHA-256, HMAC, or other cryptographic methods) before being stored or transmitted. Signed keys contain a cryptographic signature that ensures the request was made by a trusted source and hasn’t been altered. These are far more secure than simple string keys.
f2ca1bb6c7e907d06dafe4687e579fce10f3fc2aJWT (JSON Web Token) API Keys
Some APIs don’t use static keys at all—instead, they rely on JWTs (JSON Web Tokens), which contain metadata, expiration timestamps, and a cryptographic signature. JWTs are signed, encrypted, and short-lived, making them one of the most secure ways to authenticate API requests.
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyIjoxMjM0NTY3ODkwfQ.HJadklsfR5z1aA1KCustom keys with prefixes
Adds a prefix to the key (e.g. sk_ for “secret key” or pk_ for “public key”).
This allows you to differentiate between key types (public, private, test, production) and makes the system more organized and easier to debug.
sk_test_4d1f7b8a9c0d1e2f3a4b5c6dNow, let’s do a little comparison:
| API Key Format | Pros | Cons |
|---|---|---|
| Simple Alphanumeric | Easy to generate and use; works in most APIs | Easy to leak; needs restrictions to be safe |
| UUID-Based | Globally unique; standardized format | No built-in security or encryption |
| Base64 Encoded | Compatible with different systems; avoids special character issues | Easily decoded; no extra security added |
| Hashed or Signed | More secure; ensures integrity and authentication | Requires server-side verification; more complex to implement |
| JWT (JSON Web Token) | Highly secure; includes metadata, expiration, and encryption | Short-lived; requires frequent refreshing and token management |
API Key Rotation: What It Is and Why It Matters
If you’re using API keys to control access to your API, key rotation is something you can’t afford to ignore. API key rotation means periodically replacing old API keys with new ones to minimize security risks. Think of it like changing your house locks every few months—you don’t wait until a key is lost or stolen before taking action. The longer an API key remains active, the more chances it has of being exposed, whether through accidental leaks in code, log files, or unauthorized access.
Without regular rotation, an API key could be compromised and you wouldn’t even know it. This is a huge risk, especially if the key grants access to sensitive data or powerful API actions. Even if you trust your team, things happen—keys get committed to public repositories by mistake, old employees might still have access, or an attacker could be lurking, waiting for an opportunity. By rotating your API keys, you limit the damage of a potential leak. Even if a key does get exposed, it won’t be usable for long.
Best Practices for API Key Rotation
The key (pun intended) to proper API key rotation is automation. Manually changing keys across multiple applications and services is a recipe for errors and downtime. Instead, the best approach is to use a dual-key strategy—this means having two active keys at the same time: the old one and the new one. You generate a fresh key, update your systems to start using it, and once everything is working smoothly, you revoke the old key. This prevents disruptions and ensures a seamless transition.
Another good practice is to set expiration policies for API keys. Instead of letting keys live forever, enforce automatic expiration so that users are forced to generate new ones after a set period. If a user needs a long-term key, they should have to justify why instead of defaulting to permanent access.
Logging and monitoring are also crucial. Keep track of how API keys are being used, and set up alerts for suspicious activity. If an API key suddenly starts making thousands of requests per second, that’s a red flag—it could be compromised. If you’re handling sensitive operations, consider implementing scoped API keys, so even if a key is leaked, its permissions are limited to a specific function.

